
While it may be true that macOS computers are more secure than Windows-based machines, the advantage is less than you might think. Apple has done a good job of building security into macOS to stop known attacks, but the real challenge is in stopping new, never-before-seen malware (the unknowns) that can lead to ransomware or zero-day attacks. To highlight this problem, Ponemon’s Third Annual Study of Endpoint Risk reported that 80% of breaches involved new or evolved malware variants that infiltrate a system unrecognized or exploit undisclosed vulnerabilities.
Increase of ransomware attacks on macOS
In 2019, threat actors took a run at macOS and threats jumped by 60%. Since then, there have been repeated attempts and a few ransomware attacks aimed at macOS. Fortunately, we have not yet seen a major breach. In 2020, Forbes reported that Mac malware outpaced Windows by 2 to 1. In 2021, we saw an overall rise in malware developed to attack macOS like ElectroRAT, Silver Sparrow, and XLoader. These new malware strains have been paving the way for an increase in sophisticated and profitable attacks aimed at macOS, namely ransomware.
“There is still a lingering misperception that Macs are inherently more secure than Windows systems, because of the raw numbers of attacks,“ Leichter says. That sentiment is largely a reflection of the current market share, where Windows still dominates. „Macs do have some security advantages, but these are becoming less significant because of two trends: malware is increasingly targeting browser plugins, not the underlying OS,“ he adds. In addition, he says, malware developers are increasingly creating cross-platform applications independent of the operating system.
–Dark Reading, January 2022
According to the State of the Channel: Ransomware Report from Datto, MSPs have seen a rise in ransomware on both macOS and iOS devices, equating to a 500% increase from the previous year. The problem is highlighted in the 2022 Mandiant M-Trends report, where it was reported that ransomware-related intrusions have a median dwell time of five days compared to 36 days for non-ransomware intrusions.
What does this mean for defenders?
As ransomware gets faster, with the goal of quickly compromising the network and exfiltrating data, we can no longer ignore macOS. And with macOS-focused malware on the rise we predict a major successful ransomware attack in the near-term future.
Below, we highlight how and why it is necessary to plan for a future of increased attacks on macOS.
The rise of macOS in the enterprise
Perhaps the biggest reason to be concerned about a rise in attacks on macOS has to do with its increased adoption in the enterprise. Spurred by the pandemic and the move to remote work, Apple became a Big Player in Enterprise Tech this past year — and a bigger footprint equals a larger attack surface.
Mobile device management vendor Kandji conducted a survey in 2021 that showed Apple device use had grown 76% over the past two years. Gartner reported that Mac shipments were up slightly in Q1 2022 as compared to a decline in overall PC shipments. And IDC numbers in 2021 show growth in enterprise adoption as well.
„Growth in Mac usage among business users, especially for employees working remotely and given their choice of PC device, is pushing more businesses to formally adopt management tools and strategies around macOS, along with iOS/iPadOS and tvOS,” said Phil Hochmuth, program vice president, Enterprise Mobility and Client Endpoint Management, IDC.– IDC MarketScape: Worldwide Unified Endpoint Management Software for Apple Devices 2021 Vendor Assessment
macOS & ransomware: It’s about the unknowns
For known attacks, the MacOS Gatekeeper does a decent job at stopping threats that have already been exposed to the world. It’s the unknown, never-before-seen attacks that are the problem for any platform and operating system. Attackers are evolving their techniques to evade and bypass existing controls, including macOS, and they are succeeding.
There have been a few notable ransomware attempts on macOS starting with KeRanger in 2016 and Patcher in 2017. Then, in 2020, ransomware distributed through pirated software, dubbed EvilQuest, began actively targeting macOS systems. EvilQuest encrypts victim’s files, which some think is just a smokescreen, and installs a keylogger and a reverse shell to a command-and-control (C2) server and can steal any files it finds related to cryptocurrency wallets.
Ransomware remains a significant concern:
- Ransomware will cost its victims around $265 billion (USD) annually by 2031 as ransomware perpetrators progressively refine their malware payloads and related extortion activities.
- The average ransomware demand increased 144%, while the average payment increased 78%.
- Between January and March of 2022, LockBit 2.0 and Conti were responsible for 58% of all incidents and were the most active ransomware gangs so far this year.
- The fastest form of ransomware is LockBit, with a median time of just 5 minutes and 50 seconds to encrypt 100,000 files — and in one test it took only 4 minutes and 9 seconds.
- The 2022 Mandiant M-Trends report, stated that ransomware-related intrusions have a median dwell time of 5 days compared to 36 days for non-ransomware intrusions.
Unpatched vulnerabilities remain one of the top entry points to infiltrate a network. As attacks continue to grow in sophistication and frequency (a new attack occurs every two seconds) Apple will not be immune. In March 2022, Apple patched two “actively exploited” (i.e., in-the-wild, zero-day) security vulnerabilities for macOS Monterey, but the company had not released security updates for previous versions. This leaves „high confidence that CVE-2022-22674 likely affects both macOS Big Sur and macOS Catalina,“ and „nearly all vulnerabilities in the Intel Graphics Driver“ have affected all versions of macOS.
The phrase “stop it before it does damage” is often used regarding ransomware or other malware. The trouble with this mentality is that the malware is already active inside your environment. Ransomware actors are getting smarter about when they exfiltrate data or encrypt systems to avoid detection by waiting until the final stage of the attack. Once the initial malware is executed, which could be a simple backdoor or a password stealer, the threat actor identifies the infected host as part of an organization’s network. The threat actor then moves laterally across the network to deploy ransomware as the secondary attack, more potent than the first.
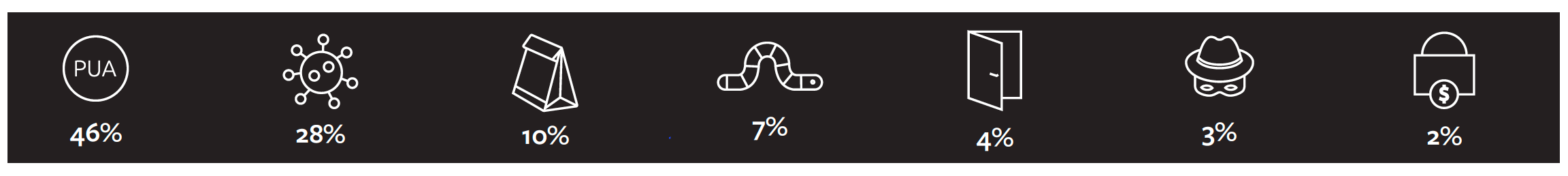
Mac ransomware protection: Deep Instinct’s advanced ransomware protection for macOS
Deep Instinct’s prevention-first approach to ransomware and zero-day threats stops attacks before they can execute on the endpoint, meaning the attackers never get the chance to drop artifacts or exfiltrate your data. With a layered defense, the Deep Instinct Prevention platform will protect your organization at the endpoint as well as your custom applications from malicious file uploads.
The Deep Instinct Prevention Platform provides the following:
- Attack prevention in <20ms, faster than the fastest ransomware can encrypt
- False positive rate of <0.1% so your team is only responding to high-fidelity alerts
- >99% unknown threat accuracy that protects your systems from new attacks and variants
To learn more about how Deep Instinct’s unique deep learning framework provides unmatched prevention for unknown and ransomware attacks, check out this video or contact us for a demonstration.
Further Reading
- https://www.deepinstinct.com/blog/3-reasons-ransomware-rollback-is-not-an-effective-strategy
- https://www.deepinstinct.com/blog/ransomware-unpatched-vulnerabilities
- https://www.deepinstinct.com/blog/healthcare-vs-hive-ransomware-how-to-protect-yourself
- https://www.deepinstinct.com/blog/deconstructing-the-revil-ransomware-attack-on-kaseya-vsa
- https://info.deepinstinct.com/tof/ransomware-prevention?_ga=2.105606282.808318644.1651786112-1559688305.1620183151
Source: Deep Instinct Blog
Fachartikel
Studien

Drei Viertel aller DACH-Unternehmen haben jetzt CISOs – nur wird diese Rolle oft noch missverstanden

AI-Security-Report 2024 verdeutlicht: Deutsche Unternehmen sind mit Cybersecurity-Markt überfordert

Cloud-Transformation & GRC: Die Wolkendecke wird zur Superzelle

Threat Report: Anstieg der Ransomware-Vorfälle durch ERP-Kompromittierung um 400 %

Studie zu PKI und Post-Quanten-Kryptographie verdeutlicht wachsenden Bedarf an digitalem Vertrauen bei DACH-Organisationen
Whitepaper
Unter4Ohren

Datenklassifizierung: Sicherheit, Konformität und Kontrolle

Die Rolle der KI in der IT-Sicherheit

CrowdStrike Global Threat Report 2024 – Einblicke in die aktuelle Bedrohungslandschaft

WatchGuard Managed Detection & Response – Erkennung und Reaktion rund um die Uhr ohne Mehraufwand












