
Executive Summary
- In late May, 2021, Microsoft and Volexity released public reports detailing recent Nobelium activity.
- Nobelium is suspected to be the new face of APT29 (aka The Dukes). We track this activity under the name ‘NobleBaron’.
- This campaign employs a convoluted multi-stage infection chain, five to six layers deep.
- Most custom downloaders leverage Cobalt Strike Beacon in-memory as a mechanism to drop more elusive payloads on select victims.
- This report focuses on NobleBaron’s ‘DLL_stageless’ downloaders (aka NativeZone)
- SentinelLabs has discovered the use of one of these DLL_stageless downloaders as part of a poisoned update installer for electronic keys used by the Ukrainian government.
- At this time, the means of distribution are unknown. It’s possible that these update archives are being used as part of a regionally-specific supply chain attack.
- We uncovered additional unreported DLL_stageless downloaders.
Overview
After the extensive revelations of Russian state-sponsored cyberespionage activities over the past five years, teams like APT28 (aka FancyBear, STRONTIUM) and APT29 (aka CozyBear, The Dukes) have retooled and reorganized extensively to avoid easy tracking by Western governments and security vendors alike. The operations of ‘APT29’ no longer look anything like they did in the past half decade. At this point our preconceptions about these groups are doing more to cloud our judgment than they elucidate. Perhaps new naming conventions (like ‘NOBELIUM’ or ‘StellarParticle’) will help piece these new clusters of activity apart– all the while upsetting folks who would prefer a simpler threat landscape than the one our reality affords us.
We track this new activity under the name ‘NobleBaron’, building off of the excellent reporting by Microsoft and Volexity. We acknowledge the suspicion that this is a newer iteration of APT29 but share in the general trepidation to equate the two. While the aforementioned companies have done excellent work exposing the inner workings of this activity, we wanted to contribute additional variants we encountered in our follow-on research, including a curious particularly insidious packaging of the ‘NativeZone’ downloader as part of a poisoned installer for a Ukrainian cryptographic smartkey used in government operations.
A Convoluted Infection Chain
As noted by Microsoft, the actor appears to be experimenting with various multi-stage infection chains. Common variations include the method of delivering the ISO containers and a wide variety of custom downloaders enmeshed with Cobalt Strike Beacon. There’s a vague mention of an iOS zero-day being hosted on Nobelium fingerprinting servers but no mention as to whether this entails an iOS payload. That said, we also suspect no company is in a position to monitor iPhone endpoints for these payloads, Apple included.
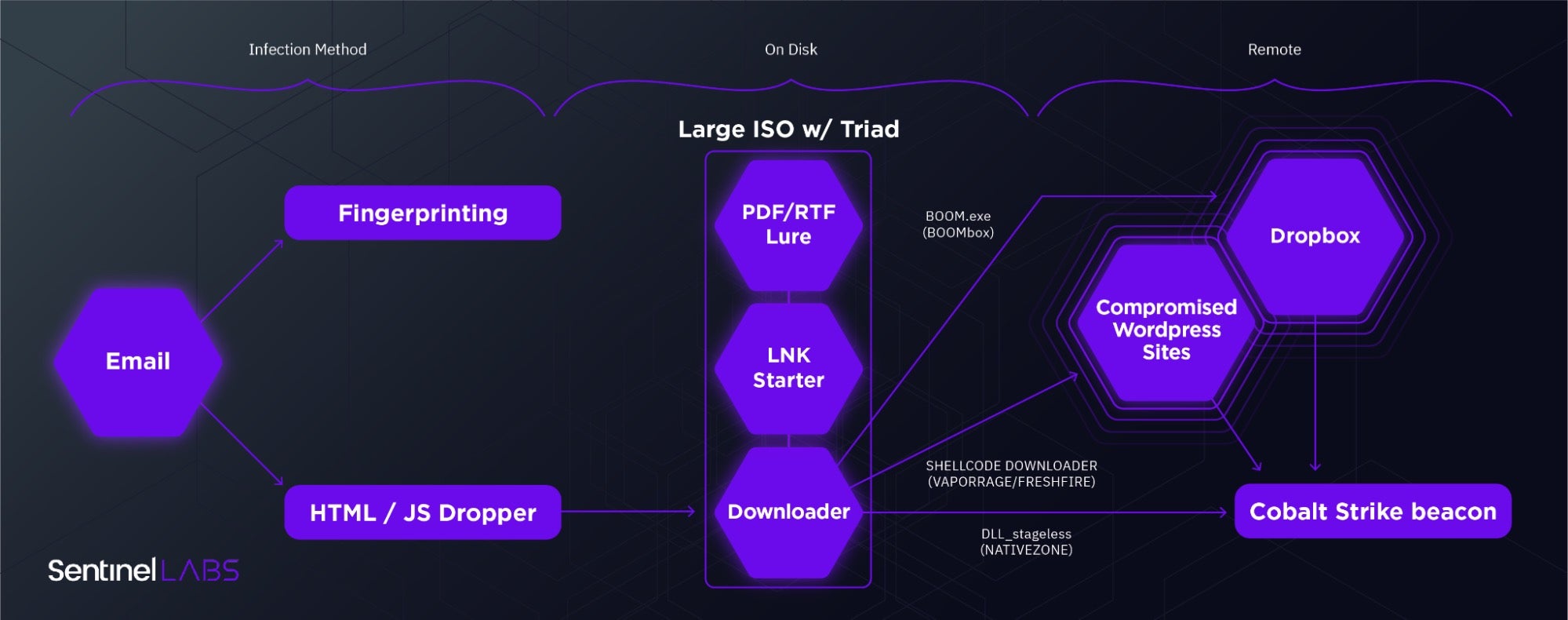
While the Cobalt Strike Beacon payload is a disappointingly ubiquitous end for such a convoluted infection chain, it’s not in fact the end of that chain. Rather, it serves as an early scout that enables selective distribution of rarer payloads directly into memory where they’re less likely to be detected. A similar technique was employed by HackingTeam’s Remote Control System (RCS) where initial infections used their ‘Scout’ malware for initial recon and could then be selectively upgraded to the full ‘Elite’ payload. After years of burned iterations on custom toolkits, it seems NobleBaron has opted for maximizing return on investment by simply lowering their upfront investment.
Notable TTPs include the following:
- An increasing depth in multi-layer droppers (a concept briefly described by Steve Miller and worth exploring further) particularly with regard to the inevitable CS Beacon payload.
- The use of large size files to avoid detection by security solutions with hardcoded size limits for ‘efficiency’.
- A fishing-with-dynamite approach to collecting initial access to victims with low-cost tooling. The SolarWinds supply chain attack is one such example of starting with a wide victim pool and whittling down to high-value targets.
Weiterlesen im Blog von SentinelOne
Fachartikel

Strategien für eine fortgeschrittene digitale Hygiene

Mit LogRhythm 7.16 können Sie das Dashboard-Rauschen reduzieren und Log-Quellen leicht zurückziehen

Wie man RMM-Software mit einer Firewall absichert

Red Sifts vierteljährliche Produktveröffentlichung vom Frühjahr 2024

Konvergiert vs. Einheitlich: Was ist der Unterschied?
Studien

Studie zu PKI und Post-Quanten-Kryptographie verdeutlicht wachsenden Bedarf an digitalem Vertrauen bei DACH-Organisationen

Zunahme von „Evasive Malware“ verstärkt Bedrohungswelle

Neuer Report bestätigt: Die Zukunft KI-gestützter Content Creation ist längst Gegenwart

Neue Erkenntnisse: Trend-Report zu Bankbetrug und Finanzdelikten in Europa veröffentlicht

Studie: Rasantes API-Wachstum schafft Cybersicherheitsrisiken für Unternehmen
Whitepaper
Unter4Ohren

Datenklassifizierung: Sicherheit, Konformität und Kontrolle

Die Rolle der KI in der IT-Sicherheit

CrowdStrike Global Threat Report 2024 – Einblicke in die aktuelle Bedrohungslandschaft

WatchGuard Managed Detection & Response – Erkennung und Reaktion rund um die Uhr ohne Mehraufwand







