Log4Shell, the latest critical vulnerability, found in the Log4j2 Apache Logging Services library, poses a serious threat to organizations + Active attempts to exploit the vulnerability were identified in the wild, currently making it the most severe threat + CrowdStrike utilizes indicators of attack (IOAs) and machine learning to protect our customers + CrowdStrike continues to track and monitor the evolution of Log4Shell and will update and deploy any countermeasures necessary to protect customers +Organizations using Log4j2 are strongly encouraged to update the library to the latest Log4j2 (2.16.0) version published on December 14, 2021 + No updates or mitigations are required for CrowdStrike Falcon deployments. For more details, customers can visit our Knowledge Base.
Recent CrowdStrike Intelligence team findings regarding the Log4Shell (CVE-2021-44228, CVE-2021-45046) vulnerabilities indicate wide-ranging impact. CrowdStrike helps protect customers from threats delivered via this vulnerability using both machine learning and indicators of attack (IOAs).
Log4Shell is a vulnerability in a prevalent Java library, found everywhere from online games to cloud infrastructure. Active and ongoing attempts to exploit the vulnerability have been observed by CrowdStrike Falcon OverWatch™. Financially motivated adversaries have quickly adopted publicly available proof-of-concept (POC) code to deploy malicious payloads on vulnerable target systems, with most deployed payloads involving XMRig miners, reverse shells, remote access trojans and botnets.
CrowdStrike uses various mechanisms to protect customers from payloads abusing the Log4j2 vulnerability. CrowdStrike Falcon’s machine learning and IOAs have been preventing post-exploitation activity since CVE-2021-44228’s disclosure.
CrowdStrike continues to actively monitor the evolution of Log4Shell and will deploy countermeasures necessary to protect customers from post-exploitation activity as a result of the Log4j2 vulnerabilities.
Vulnerability Impact and Abuse
Log4j2 is an open-source library and part of the Apache Logging Services, written in Java, and used in various frameworks such as Elasticsearch, Flink and Kafka. Since Java is a cross-platform framework, the Log4j2 vulnerability is not limited to applications running on a specific operating system.
Without proper mitigations or patching, attackers can use the vulnerability to deploy malware, reverse shells and other threats on impacted systems.
Adversaries have started conducting active scanning and exploitation attempts targeting vulnerable systems and services, regardless of the operating system, according to CrowdStrike Intelligence.
With Linux playing a critical role in cloud infrastructures, reports of payloads delivered using the Log4j2 vulnerability have revealed that botnets — such as Mirai and Muhstik — started targeting devices just days after the vulnerability became public.
Industry reports of other threats targeting operating systems and frameworks vulnerable to the Log4j2 exploitation include beacons — such as Cobalt Strike and Metasploit — being deployed in an attempt to establish a foothold in target environments.
How Customers Can Use Falcon to Hunt for Log4j2
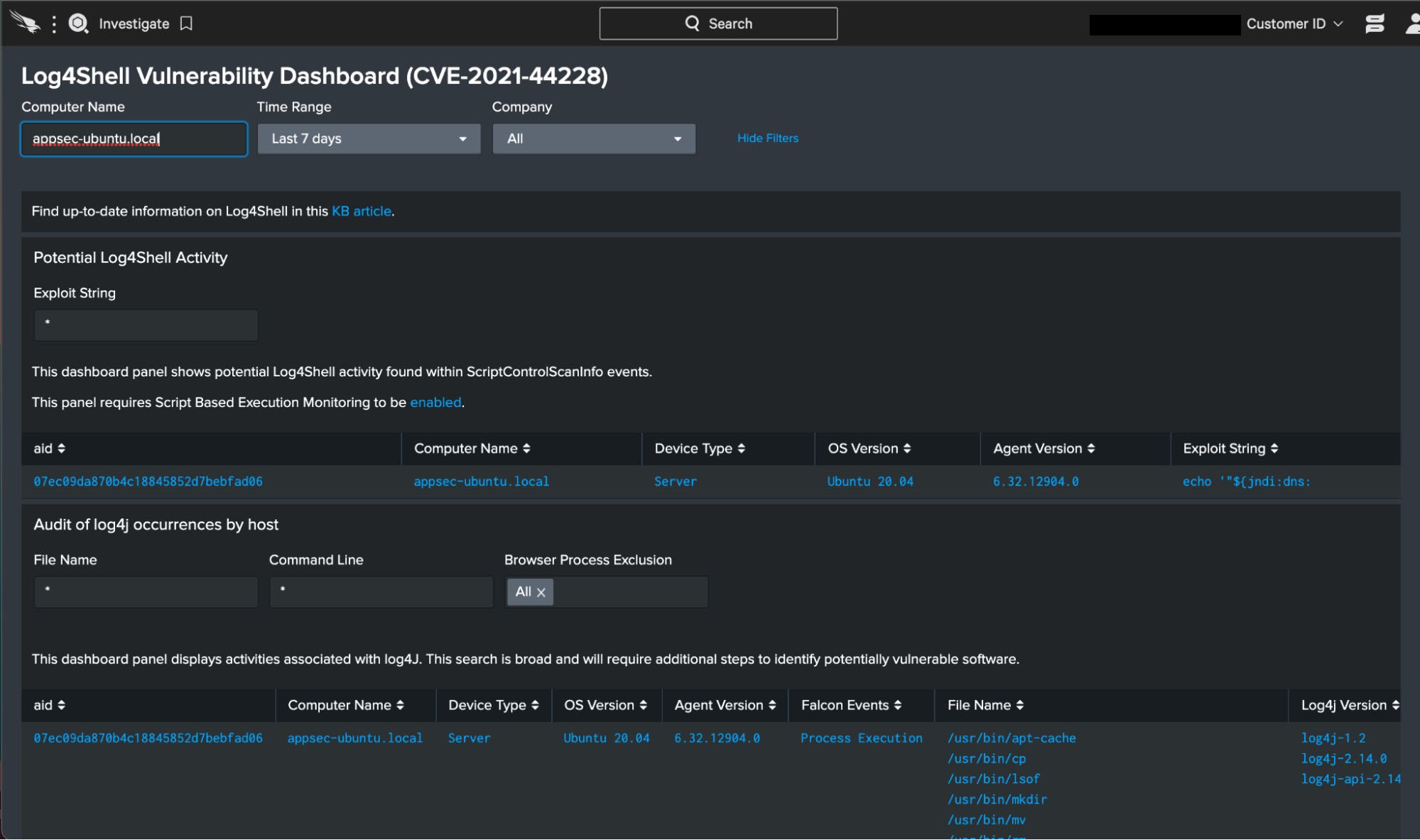
The module Log4j2 is bundled with a large number of third-party software packages. For this reason, hunting for the presence of Log4j2 will not be as simple as looking for its executable, SHA256, or file path. CrowdStrike Falcon customers can use prebuilt dashboards for all supported operating systems to identify active exploitation of the Log4j2 vulnerability in their environments.
Besides dashboards, customers can use Falcon sensor telemetry and hunt for Log4j2 invocations in ways that correspond to how developers may be using it in their applications. Here is the Falcon Insight™ query to search for Log4j2 usage:
event_simpleName IN (ProcessRollup2, SyntheticProcessRollup2, JarFileWritten, NewExecutableWritten, PeFileWritten, ElfFileWritten)
| search *log4j*
| eval falconEvents=case(event_simpleName="ProcessRollup2", "Process Execution", event_simpleName="SyntheticProcessRollup2", "Process Execution", event_simpleName="JarFileWritten", "JAR File Write", event_simpleName="NewExecutableWritten", "EXE File Write", event_simpleName="PeFileWritten", "EXE File Write", event_simpleName=ElfFileWritten, "ELF File Write")
| fillnull value="-"
| stats dc(falconEvents) as totalEvents, values(falconEvents) as falconEvents, values(ImageFileName) as fileName, values(CommandLine) as cmdLine by aid, ProductType
| eval productType=case(ProductType = "1","Workstation", ProductType = "2","Domain Controller", ProductType = "3","Server", event_platform = "Mac", "Workstation")
| lookup local=true aid_master aid OUTPUT Version, ComputerName, AgentVersion
| table aid, ComputerName, productType, Version, AgentVersion, totalEvents, falconEvents, fileName, cmdLine
| sort +productType, +ComputerName
Here is another query that looks for Log4j2 exploitation attempts:
search index=main event_simpleName=Script* cid=* ComputerName=*
| eval ExploitStringPresent = if(match(ScriptContent,"(env|jndi|ldap|rmi|ldaps|dns|corba|iiop|nis|nds)"),1,0)
| search ExploitStringPresent = 1
| rex field=ScriptContent "(?i)(?.*j'?\}?(?:\$\{[^}]+:['-]?)?n'?\}?(?:\$\{[^}]+:['-]?)?d'?\}?(?:\$\{[^}]+:['-]?)?i'?\}?(?:\$\{[^}]+:['-]?)?:'?\}?[^/]+)"
| eval HostType=case(ProductType = "1","Workstation", ProductType = "2","Domain Controller", ProductType = "3","Server", event_platform = "Mac", "Workstation")
| stats count by aid, ComputerName, HostType, ExploitString
| lookup local=true aid_master aid OUTPUT Version, ComputerName, AgentVersion
| table aid, ComputerName, HostType, Version, AgentVersion ExploitString
| rename ComputerName as "Computer Name", HostType as "Device Type", Version as "OS Version", AgentVersion as "Agent Version", ExploitString as "Exploit String"
| search "Exploit String"="***"
CrowdStrike Protects Customers Using Machine Learning and Indicators of Attack
CrowdStrike Falcon mitigations target the tactics and techniques used by adversaries and testers rather than the specific exploits being used. CrowdStrike Falcon provides coverage from various angles against malicious threats by leveraging machine learning and IOAs to target the behavior of malicious processes or scripts on an endpoint even when dealing with novel threats.
….to be continued at CrowdStrike Blog
Fachartikel
Studien

Cloud-Transformation & GRC: Die Wolkendecke wird zur Superzelle

Threat Report: Anstieg der Ransomware-Vorfälle durch ERP-Kompromittierung um 400 %

Studie zu PKI und Post-Quanten-Kryptographie verdeutlicht wachsenden Bedarf an digitalem Vertrauen bei DACH-Organisationen

Zunahme von „Evasive Malware“ verstärkt Bedrohungswelle

Neuer Report bestätigt: Die Zukunft KI-gestützter Content Creation ist längst Gegenwart
Whitepaper
Unter4Ohren

Datenklassifizierung: Sicherheit, Konformität und Kontrolle

Die Rolle der KI in der IT-Sicherheit

CrowdStrike Global Threat Report 2024 – Einblicke in die aktuelle Bedrohungslandschaft

WatchGuard Managed Detection & Response – Erkennung und Reaktion rund um die Uhr ohne Mehraufwand